Cloud Security Tips: The Ultimate Tutorial for 2025

In the rapidly evolving digital landscape, securing cloud environments is paramount. This guide provides essential cloud security tips along with comprehensive insights into cloud security architecture, best practices, and actionable checklists designed for 2025. Whether you’re new or experienced, understanding these fundamentals and advanced strategies is critical to protecting your data and infrastructure.
Cloud Security Architecture Layers Explained
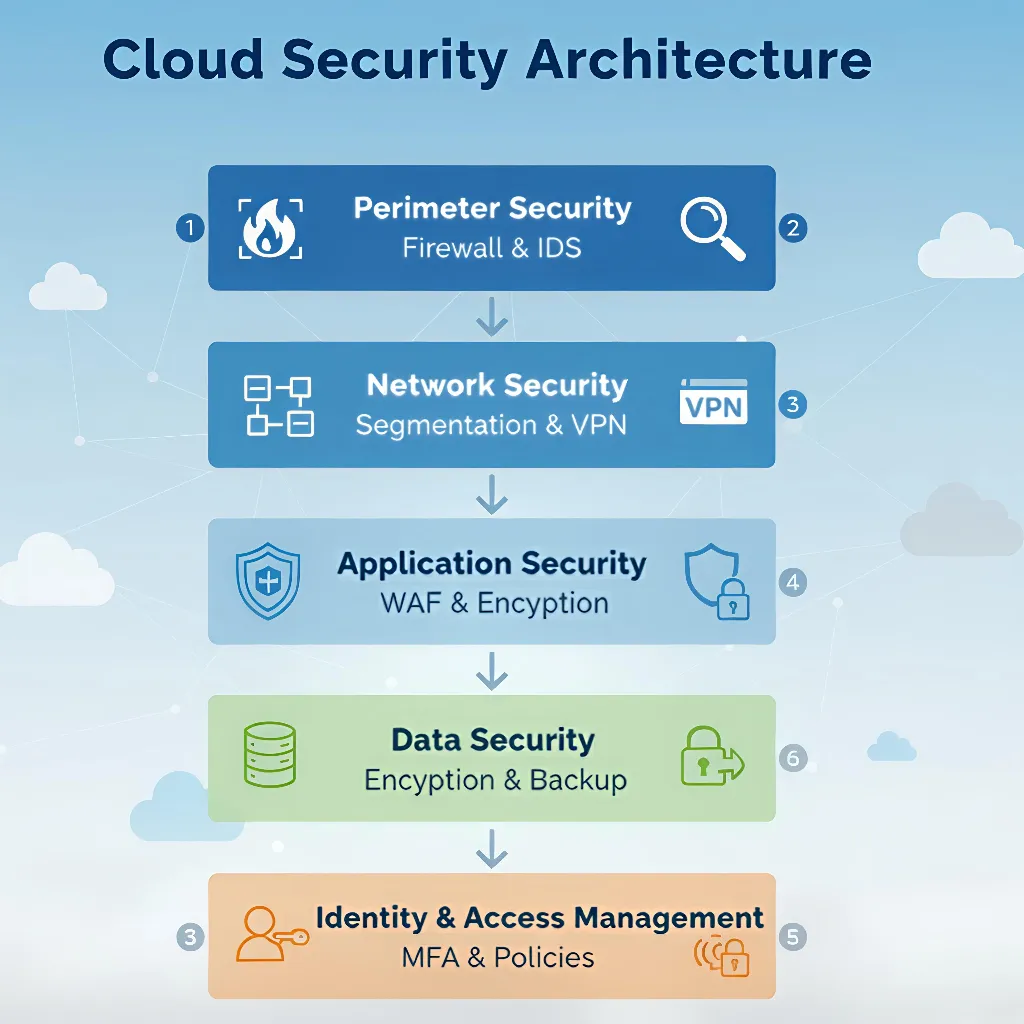
At its core, cloud security architecture is developed through a layered defense mechanism:
- Perimeter Security: Utilizes firewalls and intrusion detection systems to secure the cloud network boundary.
- Network Security: Enforces segmentation and encrypted VPN connections to isolate and protect workloads.
- Application Security: Ensures secure coding practices combined with Web Application Firewalls to guard application layers.
- Data Security: Uses robust encryption techniques and reliable backup processes.
- Identity and Access Management (IAM): Employs multi-factor authentication and strict access policies.
Properly designing security layers is vital in eliminating vulnerabilities and protecting assets against sophisticated attacks.
Essential Cloud Security Practices

Implementing certain best practices is non-negotiable for an effective cloud security program:
- Activate Multi-Factor Authentication (MFA) across all accounts.
- Encrypt sensitive data at multiple layers including in transit and at rest.
- Establish continuous monitoring and logging paired with real-time alerts.
- Enforce least privilege policies for access control and user permissions.
- Leverage Cloud Security Posture Management (CSPM) solutions for automatic configuration reviews.
- Maintain a rigorous patch management schedule for software and operating system updates.
Security Checklist for Comprehensive Protection

This checklist encapsulates critical steps to maintain robust cloud security:
- Conduct regular audits of access controls and permissions.
- Ensure detailed logging and continuous monitoring is enabled.
- Strengthen data protection through comprehensive encryption.
- Implement routine security vulnerability assessments and audits.
- Educate staff on cloud security best practices and emerging threats.
Role and Benefits of Cloud Security Posture Management
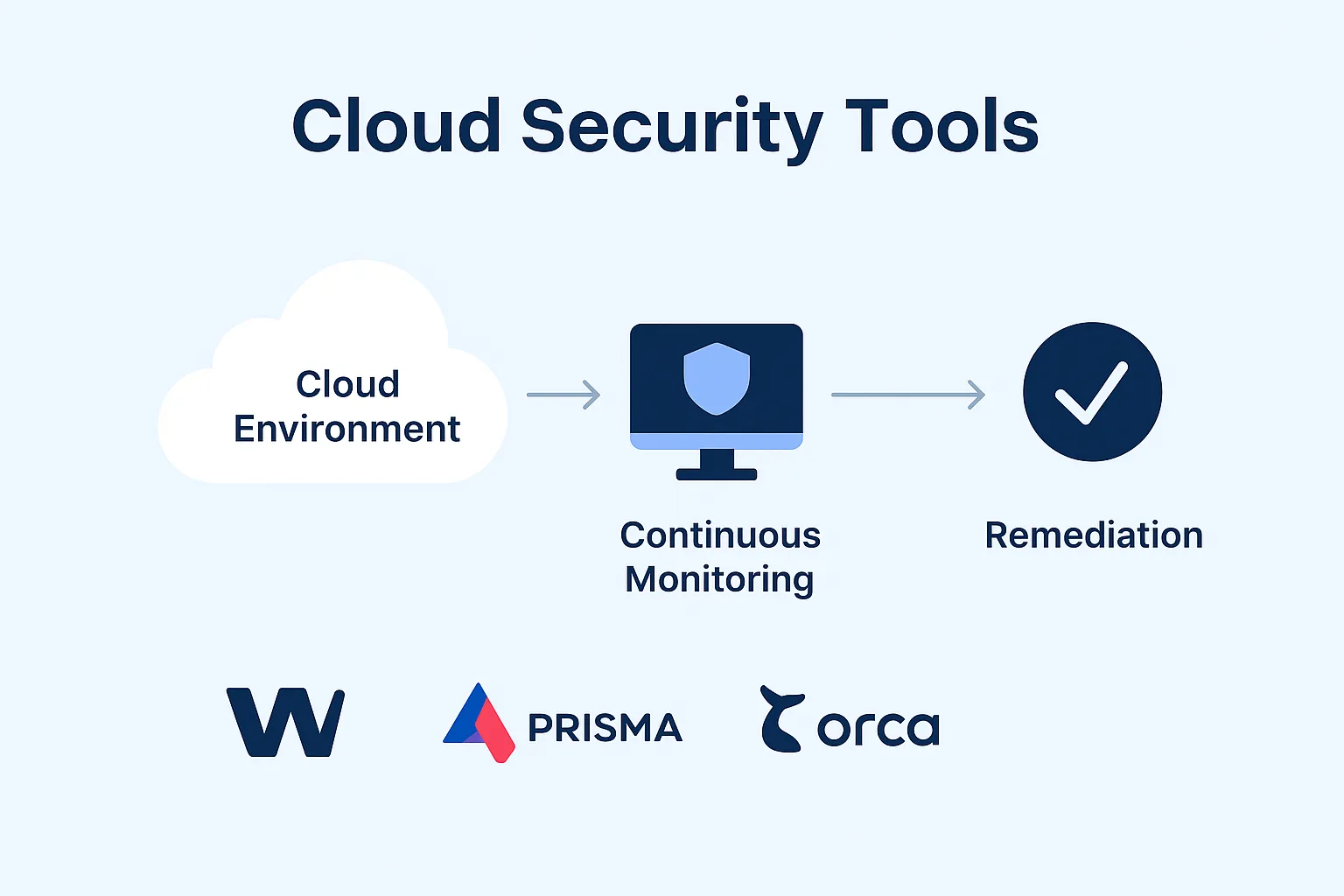
Cloud Security Posture Management (CSPM) is the modern approach to automatically evaluate cloud configurations, detect risks, and ensure compliance:
- Continuous cloud environment scanning for misconfigurations.
- Real-time alerts and compliance reporting for security teams.
- Automated remediation workflows streamline incident response.
- Integration with Security Information and Event Management (SIEM) enables centralized oversight.
Top CSPM tools include Wiz, Prisma Cloud, Orca Security, and Lacework — all critical to advanced cloud security programs.
Leading Tools in Cloud Security
Success in cloud defense relies heavily on using best-in-class tools that secure workloads and ensure compliance:
- Wiz: Cloud risk visibility and CSPM powerhouse.
- Prisma Cloud: All-in-one cloud-native security platform.
- Orca Security: Vulnerability scanning with contextual risk insights.
- Lacework: Automated behavioral anomaly detection and compliance.
Managing Hybrid Cloud Security Challenges
Hybrid cloud architectures blend private and public clouds, introducing unique security challenges:
- Consistent application of Zero Trust principles is essential.
- Deploy Secure Access Service Edge (SASE) for remote secure access.
- Maintain uniform identity and access management (IAM) policies across environments.
- Implement centralized security monitoring to unify visibility.
Explore advanced hybrid cloud tutorials at Ultimate Info Guide.
Critical Cloud Security Risks to Consider
Awareness of cloud-specific risks enables better prioritization of mitigation efforts:
- Misconfigurations potentially exposing sensitive data.
- Insider threats from compromised credentials or negligence.
- Data leakage via unsecured APIs.
- Emerging AI-powered cyberattacks.
- Failure to meet regulatory compliance requirements.
A Practical Guide for Beginners
If you’re starting out, here’s what to focus on:
- Understand shared responsibility in cloud security.
- Set up multi-factor authentication for all accounts.
- Keep abreast of cloud provider security controls.
- Train regularly with updated security resources.
Current Challenges in Cloud Security
- Keeping up with rapid cloud technology advances and integrations.
- Combating increasingly sophisticated cyber threats.
- Addressing the global shortage of skilled cloud security experts.
- Maintaining continuous compliance with evolving regulations.
The Impactful Role of Cloud Security Engineers
These professionals are the architects and guardians of secure cloud infrastructure. Their expertise bridges strategy and execution.
- Design and implement secure cloud environments.
- Manage security monitoring, incident response, and automation.
- Stay ahead through continuous threat intelligence learning.
- Earn certifications such as AWS Security Specialty and Microsoft Cybersecurity Architect Expert.
Frequently Asked Questions: Cloud Security Tips
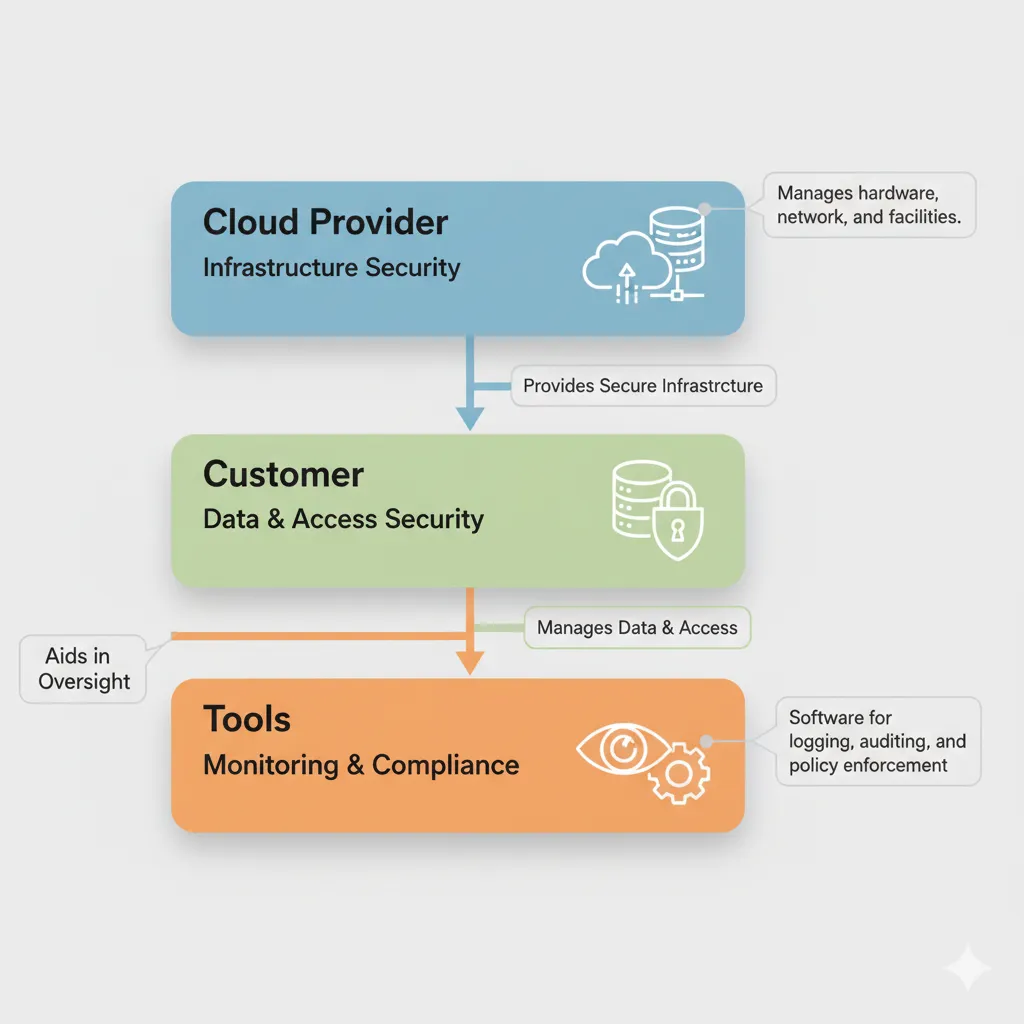
- What is the shared responsibility model in cloud security?
- It defines the distinct security responsibilities of cloud providers and customers, ensuring clarity and effectiveness in protecting resources.
- How vital is encryption in cloud security?
- Encryption guards data confidentiality and integrity both in transit and at rest, making it a cornerstone of cloud security strategies.
- What are the primary challenges of hybrid cloud security?
- Hybrid clouds introduce complexity due to varying policies, threat surfaces, and monitoring across multiple environments.
- Which CSPM tools are recommended for enterprise cloud security?
- Tools like Wiz, Prisma Cloud, Orca Security, and Lacework are widely used for continuous security posture assessments and automated remediation.
- How do I start a career in cloud security?
- Begin by understanding fundamentals such as IAM and shared responsibility, get hands-on with cloud providers, and pursue certifications like AWS Security Specialty.
This visual summary encapsulates the core cloud security principles and tips detailed throughout this comprehensive tutorial, enabling quick reference and actionable understanding.